Recently, the smart wall intrusion detection system solution independently developed by Qidian Xinyuan International Technology Development (Beijing) Co., Ltd. (hereinafter referred to as “Singularity Internationalâ€) was unveiled at the 6th China Civil Airport Security (Security) Conference and participated. During the conference, the “Manshang Airport-Ping An Airport, Smart Security†security new product new technology demonstration organized by the conference fully demonstrated the technological development of the active detection technology of the Internet of Things and its high-level application in the security field of the airport perimeter. The unanimous approval of the airport expert customers.

During the conference, Zheng Mingji, Vice President of Singular International, took the topic of “Internet of Things Security Solution†and introduced the development of the security industry and the solution of the intelligent wall intrusion detection system in detail, and shared and exchanged. related experience.
The status quo of traditional security industry - traditional technology is widely used and has many problems, and the demand for active detection technology based on Internet of things is broad.
First, the development of security industry analysis


1. Industry background: The non-traditional security threats of the whole industry are increasing, the instability factors in a few regions are increasing, and the security needs of key areas are changing to peacekeeping. Security management changes from simple detection requirements to disposal requirements, that is, the detection device needs to interface with the back-end platform and automatically trigger the disposal mechanism. The traditional security system is old, the resources are scattered, and the available resources are tight. It is urgent to integrate and coordinate the prevention and control of human defense.
2. Development trend: from the front-end mechanical detection switch to the multi-data intelligent analysis; from the passive defense emergency system to the active detection and early warning system; from a single hardware product to a partner-based professional service overall solution transformation.
Second, the smart security system architecture
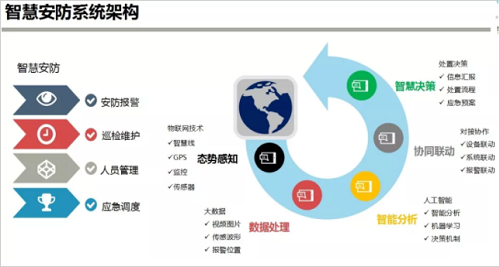
Wisdom security should have four functions: security alarm, inspection and maintenance, personnel management, and emergency dispatch. It has five technical requirements: situational awareness, data processing, intelligent analysis, collaborative linkage, and intelligent decision-making.
In other words, the essence of security is to achieve security through the means of prevention. For example, when our protection target is a self-built yard, we must first deploy active detection equipment on the wall surface to detect and report illegal personnel close to the wall. At the same time, the identification card is configured for internal legal personnel, which is convenient for legal personnel to conduct inspections and equipment inspection and maintenance. It is also possible to perform real-time positioning, trajectory tracking, zone demarcation, and inspection point setting for the inspectors to facilitate internal personnel management. When an illegal intrusion occurs, the nearest inspector is dispatched to confirm and dispose of the intrusion point through real-time location. In other words, only the above-mentioned high-efficiency coordination on four levels can achieve security.
To this end, at the front end of the prevention and control, we first need the detection and sensing technology with IoT technology to realize the situational awareness function, which covers the smart line, GPS, video surveillance, sensors and other equipment; secondly, the system needs to carry out data. Summary processing, including video pictures, sensing waveforms, alarm positions and other data; the third is intelligent analysis function, that is, intelligent analysis, machine learning, decision-making mechanism for the aggregated data through the system background server to achieve risk judgment; fourth It is the synergistic linkage, which mainly includes the linkage of equipment, system and alarm. That is to say, after the danger is judged, other systems that the system is about to link with the link will be opened; the fifth is intelligent decision-making, mainly automatic decision-making, including active information. Three aspects: reporting, triggering of the process, and initiation of the emergency plan.
Smart Wall Intrusion Detection System Solution - Chip Embedded Cable, Distributed Front End Detector; AI Algorithm, Big Data Analysis
With the changes in the security industry, the progress of science and technology has brought infinite possibilities. We have “Clairvoyanceâ€, “Shunfenger†and “Sixth Senseâ€. The sensing technology has gradually acquired the characteristics of high reliability, low latency and wide coverage. In the development of data technology, big data storage and big data mining have been continuously improved. So, what are the limitations of technology? Technology is limited. All the technologies we talk about are ideal under certain conditions, but a technology can't solve all the problems under special circumstances, and different technologies have their own strengths.


(At the meeting, the airport will visit the Singular International Live booth)
We often hear customers mention that perimeter technology needs to achieve zero false negatives and zero false positives. This seems to be very picky, but it is reasonable. As a user, he believes that it is not a risk risk or a non-threat event that keeps notifying him. This is a false positive; when there is a real threat without notifying him, this is a false negative. Different users have different perceptions and perceptions of threats, so how to satisfy them? At the same time, since technology has limitations, how can we minimize this limitation and maximize the advantages?
We believe that users are demand experts to define threats and underreports, so we need to make users become experts in requirements and define requirements. And we make the product into a customizable security system to effectively solve user-defined false positives and false negatives. To this end, we have proposed a concept: software-defined security, which is what the Smart Wall Intrusion Detection System solution is to achieve.
I. Introduction to the wisdom wall technology
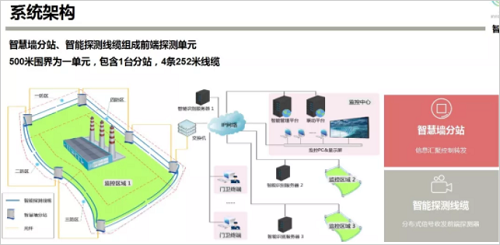
No matter how to talk about the change of security technology, it is inseparable. Only the security technology that can be applied in the field environment has vitality, otherwise it has no value. The Wisdom Wall is based on the Internet of Things AI technology to create a security ecosystem. From the highly developed technology of the Internet of Things, the centimeter-level positioning base is used to report the location of the sensor and automatically generate accurate maps.
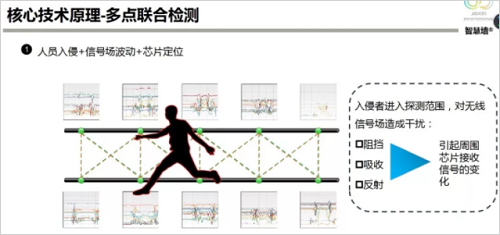
1. Technical principle: The IoT communication chip is embedded in the cable. The chip sends and receives microwave signals to form a vector, constructs a sensing detection field, and detects the field signal disturbance waveform to analyze the alarm information. It also organizes the data based on the information built by the sensor and sends all the information to the central processor; the central processor is intelligently processed and distributed to the relevant units that need to be disposed of.
At this time, the data is shared, and a common decision is made under the shared data to form an overall linkage. In other words, the entire system, AI is from the beginning to the end, is defined by software.
2, low power consumption, multi-function sensor. The intrusion detection sensor is integrated inside the intelligent detection cable, and the effective use time is up to ten years. The environment-aware sensor interacts with the detection cable for wireless data, and can continuously work for three to five years at the deployment site by using its own battery.
3. Unsupervised learning of artificial intelligence. The system is self-learning, and it can satisfy the user-defined test in the case of autonomous learning.
4. The information technology of the Internet of Everything can realize the interconnection of people, things, people and platforms, objects and things.
Second, a beautiful vision
Our good vision is that the customization is the most ideal, the customization is in line with the customer's needs, so we hope to create a "sensing + Internet of Things + intelligent software" to create a proprietary security system.
One is to build a security detection barrier, select and deploy sensors as needed.
The second is to deploy intelligent brains, deploy intelligent substations, customize alarm conditions, and train brains.
The third is to deploy a monitoring and management platform to develop monitoring and alarm information.
The fourth is to deploy monitoring terminals to realize "Wherever I am, I have to know what happened to my family, what happened to my loved ones."
Third, the system features
First, the system is inclusive. When it starts designing, it is a platform. In this platform, every sensor detection technology can be accessed. We support the sensing ecosystem. For example: visible light video surveillance, his shortcomings are basically ineffective under the conditions of night and wind and rain. For this reason, we can use infrared night vision technology as an effective supplement at night, in wind and rain, or in different lighting conditions.
/div>
The second is intelligent detection of cable sensing capabilities. The cable first constructs a wireless transmission matrix. When the spatial path is occluded, it generates an infinite path fast fading, which can determine the precise content of the intrusion and the size of the intrusion.
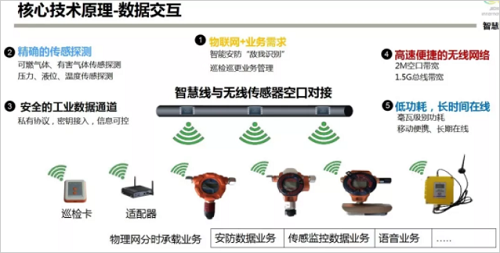
The third is intelligent identification technology. The front-end distributed vector waveform data is collected by the active intelligent detection cable, and the electromagnetic field characteristic parameters, period, mean, variance and other data are comprehensively extracted, and the AI ​​depth analysis function of the video image is combined to perform multi-dimensional AI joint judgment. The richer the front-end sensing, the richer the AI ​​processing model and the more accurate the results.
The fourth is the AI ​​intelligent judgment platform to achieve multi-sensor depth fusion judgment. Each company is an expert in judging its own technical signals, but it is not necessarily accurate for a variety of technologies. Therefore, we strive to create an AI intelligent judgment platform to support a variety of sensor depth integration.
The fifth is the Internet of Things communication platform. The intelligent detection cable of the smart wall is equal to “base station + antenna + feed + transmissionâ€, which can wirelessly detect the perception, and can access the IoT device, and can also perform data communication. The cable itself performs identification and identification of the enemy and the enemy through data interaction with the terminal. Detection, sensing, voice, video, and control data can all be transmitted interactively through the communication platform.
Sixth is active detection, three-dimensional protection. This is also a feature of our products. Its active detection range is 3 meters horizontal distance and 2.5 meters vertical height. It can prevent illegal intruders from striking through ladders and tunnels.
The seventh is to accurately locate the logical defense zone. The system has precise positioning through distributed detectors. The system can logically divide the defense zone through the intelligent management platform, which has nothing to do with the physical deployment of the device, and can set the zone timing arming/disarming mode.
Eight is the linkage device control. The system adopts dynamic modeling system pluggable system integration mode to realize the linkage of video, siren, lighting, speaker and other systems when personnel invade.
Nine is a smart inspection self-test. The system has a self-monitoring management function. All devices can display the running status in real time on the monitoring platform, and an abnormality or fault alarm occurs in time to ensure the reliability of the defense zone. The system is easy to maintain, no need to adjust the installed equipment according to seasonal changes and weather changes, and basically eliminate on-site maintenance.
Related Links
Singular International is a subsidiary of Beijing Shenzhou Taiyue Software Co., Ltd. (referred to as Shenzhou Taiyue). The main business of Shenzhou Taiyue is concentrated in ICT operation and maintenance management, Internet of Things and communication (including Internet of Things security), artificial intelligence and big data. Four major areas. Singular International is a national high-tech enterprise, an innovative enterprise specializing in the research and development of core technologies for communication and Internet of Things. The Smart Wall Intrusion Detection System solution developed by Singular International has been applied and tested in the fields of energy, airport and cultural relics protection. In the airport field, after two years of joint development, Singular International and Xi'an Xianyang Airport have realized the dynamic monitoring system for the perimeter alarm, realizing the whole process of the perimeter perimeter prevention, from discovery, tracking to disposal, all-weather, strict discrimination and low False positives, multiple levels, and multiple means of discrimination. At the same time, it also realized the airport's quick response and multi-method emergency response methods, such as lighting, broadcasting, police lights, and the results of system linkage.

(Singularity International participated in the Mangshi Airport - "Ping An Airport, Smart Security" demonstration project site, and on-site introduction)
Technology has won attention and honor. At present, Singular International has more than 130 PCT patents and 78 invention patents at home and abroad. Zhongguancun 10 major scientific and technological innovation products, Beijing Science and Technology Award.
It is believed that with the development of Internet of Things technology, the defined IoT security system can be stronger, richer and fuller, and can better contribute to the security of civil aviation.
We provide high precison CNC Machining part custom-made service
Main process: Precision CNC machining part
Material:Aluminium6061/6063/7075/5052 etc, Stainless steel303/304/400/316, SteelQ235,20#,45#etc,
Brass:C36000(C26800), C37700(HPb59), C38500(HPb58),C2200(CuZn37),C28000(CuZn40) etc,Copper;Beryllium bronze copper.
Process:CNC turning,CNC milling, CNC grinding;CNC Lathe machining, CNC boring;CNC drilling, surface treatment
Surface treatment:Hardness anodizing black/clear, steel oxidizing dark-blue, electro-polishing, electroless nickel plating, silver plating, golden plating etc
Tolerance:+/-0.001mm or +/- 0.00004"

CNC Machining
CNC Machining,CNC Milling Machine,Milling Machine,CNC Mill
Baoding Henglian Mechanical Co.,Ltd , https://www.hengliancasting.com











